How companies are coping with intentional adulteration rule enforcement
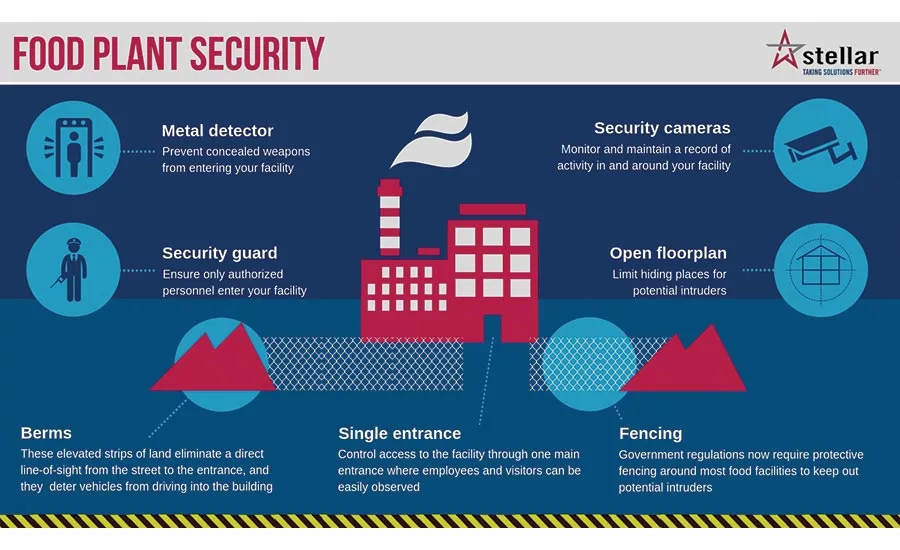
Infographic courtesy of Stellar

Processors are explaining defensive measures—and more importantly why they’re needed—as a key part of employee training.
Photo courtesy of Getty Images
Processing plants are locking tanks, installing more surveillance cameras and investing in defense training to beef up protections against people who might try to taint food, especially workers with a grudge.
Food defense plans are in full swing for large companies with enforcement starting in March, while smaller businesses are in the thick of finding the best protection methods ahead of their deadline this summer.
A big part of implementing a food defense plan is deciding between expensive technology and cheaper, low-tech strategies to protect your product from intentional adulteration. As your operation considers the many available options for equipment and monitoring, let’s explore what you need to know to choose the right solutions without overspending.
While the government says a food defense plan should prevent wide-scale public harm, processors have a much higher risk management standard because they know that even a few injuries from tampering could cause catastrophic brand damage, says Frank Pisciotta, president of Business Protection Specialists Inc. security consultants.

“Companies can be FDA compliant but still have major exposure to intentional adulteration.”
–Frank Pisciotta,
president of Business Protection Specialists Inc.
The IA rule is “by no means a silver bullet,” and companies can be FDA compliant but still have major exposure to intentional adulteration, he says.
For example, if someone drops a few pieces of broken glass on seafood cans traveling down a conveyor belt, that could substantially injure the brand when consumers discover the glass and the media reports on it.
“Compliance with the IA rule does not assure any organization a solution for comprehensive food defense,” he says.
Looking for quick answers on food safety topics?
Try Ask FSM, our new smart AI search tool.
Ask FSM →
In other words, many plants have had extensive food defense measures for years.
Scott Baesler, senior project manager and engineer at design and construction firm Stellar, describes food defense as a subpart of good manufacturing practices. Most large and medium companies have some form of GMP program, though smaller businesses often find the expense prohibitive. That’s because implementation usually involves a large paradigm shift in the way employees operate, as well as substantial technical knowledge about the program’s contents.
Food defense is often an important element in Stellar’s strategic design projects and overall GMP planning. Most of Stellar’s customers have focused on food defense for facilities outside the U.S., even though a large part of food defense exists in their GMP programs. “Most elements of a solid GMP program can easily be modified to address many aspects of food defense without overspending,” he says.
The majority of food defense operations can be handled with well-defined operating procedures on all levels of the process, according to Baesler. “There is a cost associated with implementing these programs, but there is also a cost associated with not implementing them.” Some of the more expensive food defense items include better security technology and track-and-trace systems, he notes.

“Processors can easily modify elements of a solid GMP program to address food defense.”
–Scott Baesler,
senior project manager and engineer at Stellar
The place to start
A food defense plan begins with a vulnerability assessment, and Pisciotta’s consulting firm favors what the FDA calls the key activity type approach.
The FDA looked at 50 vulnerability assessments to rank four types of activities as the most at risk:
- Bulk liquid receiving and loading
- Liquid storage and handling
- Secondary ingredient handling
- Mixing and similar activities
The approach considers three factors outlined in the law: public health impact, accessibility and feasibility to contaminate, Pisciotta notes. The method provides “an opportunity for companies to rightfully disqualify a point step or procedure for practical reasons.”
FDA guidance released in March 2019 provides a worksheet to determine public health impact and calculate the volume of food at risk. It helps facilities figure out the amount of a contaminant that would create a lethal dose in a serving size.
“Generally speaking, the larger the batch size, the more contaminant is required to create a lethal dose,” he says. “At some point, companies can conclude that it would not be feasible to introduce a certain amount of contaminant undetected.”
Earl Arnold, global manager for food defense and FSMA, AIB International, says some companies select the key activity type assessment because it is easier to use, and training is very simple for the individual conducting the assessment. However, some facilities miss the requirement that if they have a key activity type within a processing step, that step is then required to have implemented mitigation strategies, unless they go back and combine or use the hybrid method and can further justify how it is not considered actionable.
Some facilities are electing to use additional CCTV cameras and monitoring these activities, and others use electronic access, requiring additional purchases, Arnold says. Some facilities are selecting other low-cost options, such as securing areas with traditional locks or seals and supervisory monitoring.

“Two defense approaches: technology investments that free up labor or low-cost monitoring that needs more worker time.”
–Earl Arnold,
global manager for food defense and FSMA, AIB International
Defense on a budget
Companies typically have two ways to approach mitigation strategies: technology solutions that are expensive but require less labor or low-cost methods that require more employee time, Arnold says.
For example, one way to monitor people using CCTV cameras could be to review footage three times per shift, fast forwarding at a defined speed. If no issues are observed and the review is documented, this mitigation strategy is complete.
For a low-cost option, employees in a sensitive area could wear red shirts. A supervisor would monitor this by inspecting the area three times per shift, documenting the results. If someone who wasn’t wearing red was identified, corrective actions can be taken. “This option will require a little more work and training to implement,” Arnold says.
“To ensure a robust defense plan without overkill, you first need to be able to think like a criminal,” he says. “Once you can do this then developing mitigation strategies becomes easier.”
Pisciotta says the FDA underestimated the cost of compliance in some cases. “I see every business struggling on the cost side.”
His company’s consulting ensures compliance while minimizing costs by making sure processors do not use unnecessary actionable process steps, he says. In some cases, consultants have reduced actionable process steps by 90%, a huge costs savings for manufacturers with very low profit margins.
His consultants help companies chose low-cost measures versus more expensive physical security that he says can be ineffective. For example, he notes the FDA seems very interested in using cameras as a defensive measure. “Cameras are not a good mitigation strategy, and while good for after-the-fact investigation, they do next to nothing to prevent an incident,” he says. He feels similarly about increased security lighting as a food defense strategy.
Arnold says early in the development of the food defense program, large companies wanted to use a lot of technology for mitigation strategies and thought a large amount of capital was required. As guidance documents became available and the FDA clarified its requirements, companies moved to a more balanced approach of low-cost, labor-intensive strategies and technology-based solutions.
An adequate defense
When determining whether a defense measure is needed, first consider whether you can document that mitigation strategy, Arnold advises. Defense strategies require procedures for monitoring, corrective actions and verification.
“I recommend realistically reviewing and determining whether the activity will significantly reduce the potential of the vulnerability that was identified,” he says.
For example, if you use a lock to secure a tank lid to prevent tampering, this implies that you’ll have a key control policy and log. You’ll need to identify who needs access and provide them the key, determine how often to monitor, and ensure the lock is in place. Will a monthly review of the lock suffice? What about every quarter? This depends on how often access to the tank is needed, he explains.
And if a plant identifies the need for locks, Arnold suggests considering seals (bolting or clamping them down) and a log instead. This will help minimize the need for a key control program and should not require a lot of capital for numerous locks and replacement keys.
Baesler suggests to Stellar clients that they answer these questions to determine if a defensive measure is adequate:
- Is every person who enters or leaves the facility—or particular areas—traceable at all times?
- Are all raw materials verified according to the plan before entering the process?
- Do you understand the backgrounds of each employee you have hired? Have you hired any who may pose a threat under certain circumstances?
- Can you validate the quality and safety of each product shipped from the plant?
Training the defense team
Facilities of all sizes are still refining their training and mitigation strategies or are in full development mode, Arnold says. Most large companies have identified and trained their food defense qualified individuals, and they’re now understanding that having one FDQI is not enough and backups are needed. They are also training their food defense team members and supervisors.
Medium and small businesses are getting their main personnel trained in the requirements. Usually after attending a training session, people ask questions about how to educate others and what resources are available.
There are many ways to do the training through FDA-recognized courses developed by the Food Safety Preventive Controls Alliance.
You can take FDQI online courses on specific skills:
- Conducting key activity type vulnerability assessment
- Developing mitigation strategies
- Preparing and reanalyzing a food defense plan
- Conducting the vulnerability assessment using the three-element or hybrid methodology
AIB International developed a two-day course that focuses on the regulatory requirements and includes training on a range of FDQI topics. AIB offers a variety of courses that prepare all levels of employees to lead and support food defense efforts. These sessions are delivered in live, virtual classroom formats that meet people’s needs for high-quality training without traveling or its related costs.
Specifically, AIB’s Food Defense Coordinator Online course challenges trainees on how they would handle intentional adulteration in their food plants, he says.
AIB recommends a four-level training program to meet all requirements:
- Food defense qualified individual training—Whether you have one main FDQI or break it down into three responsibilities, AIB encourages backups.
- Supervisors and/or managers—They should be trained on the overall requirements, conducting food defense corrective actions and verification activities, as well as trained in any mitigation strategies they supervise.
- Personnel conducting the mitigation strategies or food defense monitoring—They should understand what they are required to monitor, how to document it and what to do if a deviation occurs.
- All personnel—Everyone needs basic food defense training.
To encourage buy-in with employees, Arnold suggests including examples of IA issues from the past in training to demonstrate why these new steps are important. A good food safety and food defense culture can go a long way, he says. “When management demonstrates the importance of these programs, employees will too.”
Pisciotta says companies should go beyond the basic training to help employees look out for a threat from someone they work with. Most recent cases of intentional adulteration have involved an insider with a grievance, and the FDA emphasizes the inside threat or “radicalized insider,” he notes.
“An effective food defense training program has to feature some component for employees to recognize insider threats, particularly when you look at a number of the food contamination incidents that have occurred in the past few years.”
Smaller companies
How aggressively a plant pursues GMP and food defense measures typically depends on the industry, Baesler says. “Overall, smaller businesses seem to be doing what they can to ensure food safety.”
The hemp and CBD industry offers a prime example, he says. Until fairly recently, the industry has been mostly nonregulated, but now the USDA is drafting regulations for these companies. Many have turned to GMP certification to get a jump on the requirements so they’re not facing an overhaul all at once when the agency finalizes regulations.
The industry has seen many cases of food negligence that caused negative consumer health effects, Baesler says. “Although none of these cases have been tied to the food defense issue thus far, this demonstrates how neglecting GMP guidelines could very easily become an issue.”
Early enforcement
Pisciotta says the first enforcement starting in March for large companies will be “quick check inspections,” and facilities need to ensure they meet the basics requirements: a proper vulnerability assessment, a defense plan that’s being maintained and staff training. “The enforcement is not going to be that strict.”
The early inspections will not involve a “deep dive” on mitigation strategies, which companies continue to fine-tune, he says. Strategies that require capital investment may take a year to cycle through, he notes. The FDA did an informal preliminary review of a food defense plan that Pisciotta’s company wrote and was happy with the results.
The experts expect food companies will go through a second wave of food defense planning as they need to modify their plans to prepare for inspection or once they hear inspectors’ feedback.
Further Reading:
►How companies defend themselves
►For some processors, protection extends to transport
For more information:
AIB International, www.aibinternational.com
Business Protection Specialists, www.securingpeople.com
Stellar, www.stellar.net








